Page 42 - RC2020-EDGEMagazine_SummerEdition
P. 42
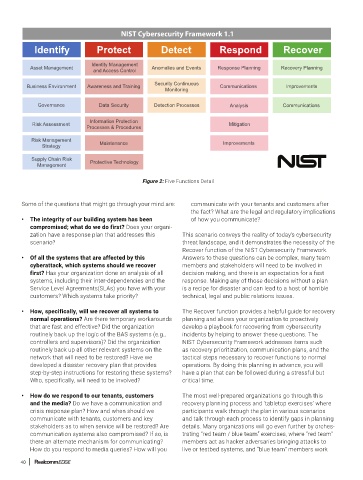
NIST Cybersecurity Framework 1.1
Identify Protect Detect Respond Recover
Identity Management
Asset Management Anomalies and Events Response Planning Recovery Planning
and Access Control
Security Continuous
Business Environment Awareness and Training Communications Improvements
Monitoring
Governance Data Security Detection Processes Analysis Communications
Risk Assessment Information Protection Mitigation
Processes & Procedures
Risk Management Maintenance Improvements
Strategy
Supply Chain Risk Protective Technology
Management
Figure 2: Five Functions Detail
Some of the questions that might go through your mind are: communicate with your tenants and customers after
the fact? What are the legal and regulatory implications
• The integrity of our building system has been of how you communicate?
compromised; what do we do first? Does your organi-
zation have a response plan that addresses this This scenario conveys the reality of today’s cybersecurity
scenario? threat landscape, and it demonstrates the necessity of the
Recover function of the NIST Cybersecurity Framework.
• Of all the systems that are affected by this Answers to these questions can be complex, many team
cyberattack, which systems should we recover members and stakeholders will need to be involved in
first? Has your organization done an analysis of all decision making, and there is an expectation for a fast
systems, including their inter-dependencies and the response. Making any of those decisions without a plan
Service Level Agreements(SLAs) you have with your is a recipe for disaster and can lead to a host of horrible
customers? Which systems take priority? technical, legal and public relations issues.
• How, specifically, will we recover all systems to The Recover function provides a helpful guide for recovery
normal operations? Are there temporary workarounds planning and allows your organization to proactively
that are fast and effective? Did the organization develop a playbook for recovering from cybersecurity
routinely back up the logic of the BAS systems (e.g., incidents by helping to answer these questions. The
controllers and supervisors)? Did the organization NIST Cybersecurity Framework addresses items such
routinely back up all other relevant systems on the as recovery prioritization, communication plans, and the
network that will need to be restored? Have we tactical steps necessary to recover functions to normal
developed a disaster recovery plan that provides operations. By doing this planning in advance, you will
step-by-step instructions for restoring these systems? have a plan that can be followed during a stressful but
Who, specifically, will need to be involved? critical time.
• How do we respond to our tenants, customers The most well-prepared organizations go through this
and the media? Do we have a communication and recovery planning process and ‘tabletop exercises’ where
crisis response plan? How and when should we participants walk through the plan in various scenarios
communicate with tenants, customers and key and talk through each process to identify gaps in planning
stakeholders as to when service will be restored? Are details. Many organizations will go even further by orches-
communication systems also compromised? If so, is trating “red team / blue team” exercises, where “red team”
there an alternate mechanism for communicating? members act as hacker adversaries bringing attacks to
How do you respond to media queries? How will you live or testbed systems, and “blue team” members work
40