Shadow IT: The Hidden Threat to Real Estate Companies

Uncover, Manage, and Combat the Security Risks of Unauthorized Technology
In today's rapidly evolving technological landscape, the emergence of Shadow IT poses significant challenges for organizations, particularly in the commercial real estate sector. Shadow IT occurs when employees utilize technology without formal approval from the IT department, leading to potential security, compliance, and data integrity risks.
For real estate companies, unauthorized technology use can manifest in various ways, from an employee maintaining lease contracts on an Excel spreadsheet to teams leveraging project management software for task communication. According to Cisco, a staggering 80% of employees engage in Shadow IT, often believing they are enhancing productivity or addressing specific business challenges that current systems fail to resolve. However, this trend exposes organizations to numerous risks, including data silos, inefficiencies, compromised security, and potential violations of data protection laws.
Understanding the Data and Security Risks
The adoption of Shadow IT can inadvertently lead to significant company-wide vulnerabilities:
- Compromised Data Security – When data resides across multiple personal devices and disparate software solutions without oversight, the risk of unauthorized access and data breaches escalates dramatically.
- Failure to Meet Compliance Standards – Utilizing unapproved software can result in non-compliance with industry regulations. IT leaders can only mitigate this risk by maintaining visibility into all technology utilized within the organization.
- Lack of Support and Maintenance – Without designated oversight, critical data can be lost when employees depart or take leave. If IT is unaware of the tools in use, they cannot provide the necessary support or maintenance, leaving the organization exposed.
- Integration Challenges – Integrating unauthorized technologies with existing infrastructure can be both time-consuming and costly, further complicating the IT landscape.
Strategies for Management and Prevention
To effectively combat Shadow IT, a proactive approach is essential. Educating employees about the associated risks and introducing approved technologies is vital, as many may be unaware of the potential repercussions.
While some teams may have the autonomy to procure their own tools, the responsibility for maintaining these technologies ultimately falls on the dedicated technology function of the business. This necessitates a collaborative approach between the technology team and business operations, emphasizing regular communication and IT audits. Establishing clear data and technology platform governance policies will provide employees with a framework for implementing new solutions responsibly.
Adopting a Proactive Approach
As Software as a Service (SaaS) solutions proliferate, Shadow IT will continue as an increasingly prevalent issue within real estate firms. At RealFoundations, we help clients identify and mitigate unauthorized technology use through comprehensive assessments of their technology platforms and the development of strategic roadmaps with targeted initiatives.
By fostering a culture of awareness and collaboration, organizations can better manage the risks associated with Shadow IT, ensuring that their technological infrastructure remains secure and efficient.
Safeguard Your Real Estate Business from Shadow IT Threats
Discover how to identify, manage, and mitigate unauthorized technology with RealFoundations' expert insights. To learn the measures you can take to stay compliant, secure, and efficient, and begin the process of integrating any new programs into your existing tech stack PROPERLY, connect with one of our technology experts today.
This Week’s Sponsor
RealFoundations is the world’s foremost professional services firm focused solely on the real estate industry. Through delivery of Management Consulting and Managed Services, we help companies that develop, own, operate, service, or invest in real estate make better, more profitable decisions. We make real estate run better.
Read Next
 3/27/2025
3/27/2025
The Convergence of Edge Computing, Cloud, and AI in Building Automation and Smart Buildings In the built environment, we have seen the convergence of Operational Technology (OT) and Information Technology (IT), later expanding to include Workplace Technologies (WP).
 3/27/2025
3/27/2025
DC Power: A Holistic Approach to Energy Savings in Commercial Buildings In today's energy-conscious world, businesses constantly seek ways to reduce their carbon footprint and operational costs.
 3/13/2025
3/13/2025
How to Achieve Eco-Friendly Facility Management Commercial real estate operators and facility managers are focusing on sustainable practices to minimize environmental impact, create healthier workplaces, improve productivity and lower operational costs.
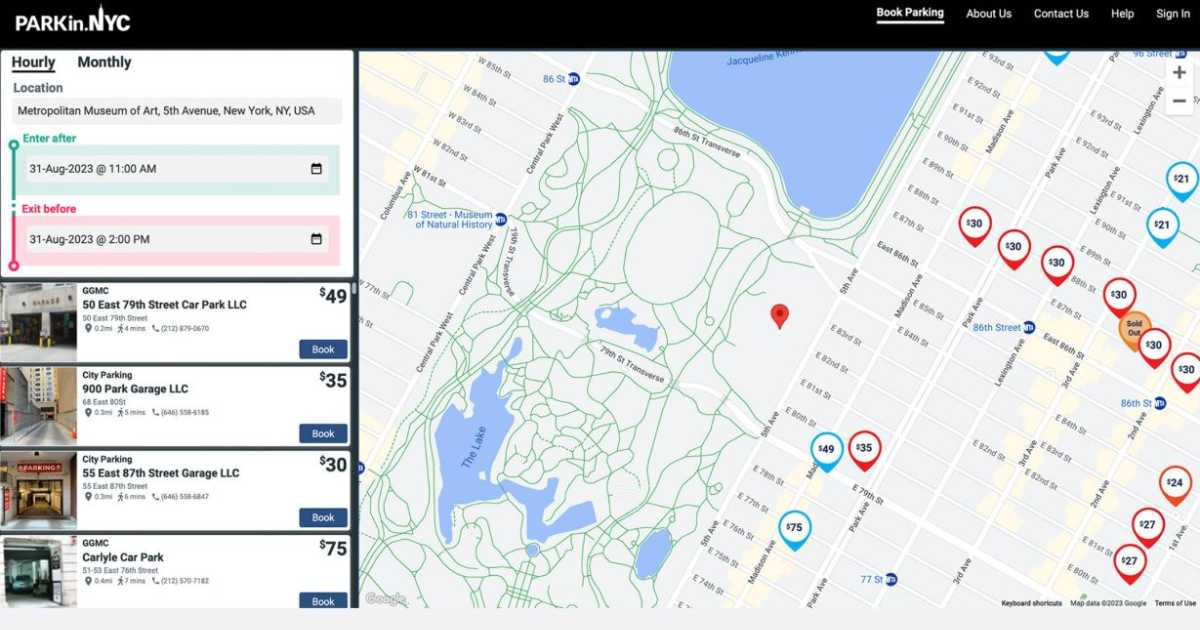 1/23/2025
1/23/2025
When It Comes To Managing Properties’ Parking, Technology Is Key It’s easy for developers and real estate owners to think of parking as a necessary evil. They know they have to provide it (often, because it’s mandated by code), they understand that prospective tenants and buyers expect to be provided parking, but they haven’t figured out how to maximize its value.




.gif)




