Page 19 - REALCOMM EDGE-Fall 2017-FINAL
P. 19
“We live in an age where cyber mischief, crime and even
terrorism is in the news every day. Overall cyber crime
damage will hit $6 trillion by 2021 and ransomware
alone will cost $6 billion in 2017.”
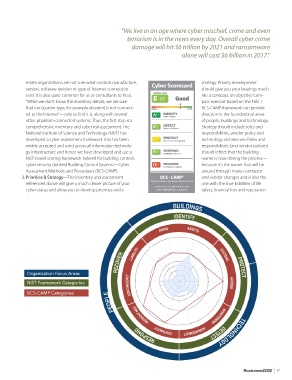
estate organizations are not sure what controls manufacture, strategy. Priority development
version, software revision or type of Internet connection should give you your bearings much
exist. It is also quite common for us as consultants to hear, like a compass; an objective ‘com-
“While we don’t know the inventory details, we are sure pass exercise’ based on the NIST /
that our (system type, for example elevator) is not connect- BCS-CAMP framework can provide
ed to the Internet”—only to find it is, along with several direction in the foundational areas
other phantom-connected systems. Thus, the first step is a of people, buildings and technology.
comprehensive inventory and cyber risk assessment. The Strategy should include roles and
National Institute of Science and Technology (NIST) has responsibilities, vendor policy and
developed a cyber assessment framework that has been technology architecture. Roles and
widely accepted and used across all information technolo- responsibilities (and vendor policies)
gy infrastructure and hence we have developed and use a should reflect that the building
NIST-based scoring framework tailored for building controls owner is now driving the process—
cyber security dubbed Building Control Systems—Cyber because it’s the owner that will be
Assessment Methods and Procedures (BCS-CAMP). around through many contractor
2. Priorities & Strategy—The inventory and assessment and vendor changes and is also the
referenced above will give a much clearer picture of your one with the true liabilities of life
cyber status and allow you to develop priorities and a safety, financial loss and reputation
Realcomm 17