The Legal Implications of Commercial & Corporate Real Estate Digital Transformation

Potential risks, liabilities and contractual nuances should be a primary concern for commercial and corporate real estate owners who seek Digital Transformation. Owners should consider how laws related to data, privacy and cybersecurity frame the scope of Digital Transformation.
Assessment of applicable legal boundaries can help owners develop a framework for a transformation that incorporates risk avoidance and preservation of opportunities during third party contract negotiations. Additionally, attention to such legal implications can improve organizational agility and flexibility by enabling the development of a cache of legal documents designed to simplify and incorporate third party services without extensive negotiation or unnecessary assumption of risk.
Regulatory Considerations
An owner may contemplate a Digital Transformation that includes activities like the collection and analysis of data, which are subject to local, state, or federal regulation. As with any entrepreneurial endeavor, owners should understand a new regulatory environment prior to entry. For example, a portfolio real estate owner may determine that it will upgrade all security systems to incorporate advanced analytics, machine learning and third party facial recognition services. The property owner could face potential liability if portfolio tenants are healthcare providers and the system operate in a way that violates patientsí rights under HIPAA. Failure to observe regulatory requirements could result in fines and potential criminal liability. As part of a Digital Transformation, an owner may want to evaluate the unique circumstances of existing properties, tenants and agreements to identify whether any regulatory schemes could limit the collection and retention of data or other digital activities as well as an effort to avoid regulatory risk determine whether a digital benefit is outweighed by cost of compliance.
Contracts
Owners should examine the impact of new technologies in contract negotiations and recognize that technology will advance rapidly during the term of existing and future agreements. A digitally resilient approach to contract negotiation could focus on the management of interests, activities and relationships of the parties to the contracts with respect to the creation, collection, interpretation and sharing of data arising from or with respect to the property or parties subject to agreement. Prudent owners should consider contractual provisions that will account for the occurrence of data incidents like a cyber attack or data leak, in commercial financing documents, purchase and sale agreements, and leases. Simple tweaks to widely accepted standard language can provide significant protection, if a data incident occurs, by eliminating ambiguity that could result in costly litigation. For example, parties to a purchase and sale agreement could agree that failure of either party to perform because of a data incident is not a default of the contract and that the parties agree to cooperate and proceed to closing in such an event.
Owners with Digital Transformations that incorporate third party services require contracts that allow the sharing of customer or tenant data, without additional liability, or loss of control. To avoid negotiation bottlenecks an owner may develop a standardized collection of service contracts including non-disclosure, privacy, indemnification and agency agreements with third party service providers to test relationships during short-term feedback loops. Without the ability to engage in feedback loops and share data quickly and security, an owner may struggle to keep up with the pace of digital markets.
Cybersecurity
Cybersecurity should be a top priority of any Digital Transformation strategy. While traditional cyber risk assessments focus on the value of data, the significant business interruption that accompanies a data incident like a cyber attack or a data leak has the potential to severely disrupt real estate operations and obligations. Perhaps even more significant, however, are the security risks that may accompany the utilization of systems that automate and control real world places.
As technology evolves, many owners will implement building control systems to reduce costs and optimize efficiency. Significant concerns abound regarding security of IoT devices. Unlike cyber attacks on data, attacks on building control systems can result in real world consequences including disruption, damage and death. Owners should consider threats to building control and automation systems as categorically similar to public infrastructure and utility threat, and invest significant time and resources into the deployment of systems that are designed to be secure. For example, a developer or property owner may want to carefully assess whether remote control and automation of systems like fire suppression, elevators, door locks and other critical components offsets the potential negative impacts that could occur if such systems are manipulated. Furthermore, great efforts should be taken to monitor and maintain the security and integrity of such systems to avoid unwanted and unintended consequences.
Cyber Insurance and Practical Approaches
Fortunately, many of the existing and emerging cyber risks are covered by cybersecurity insurance policies. Digital Transformation should include careful study of available cybersecurity policies and appropriate policy limits. Owners will want to be sure that appropriate third party policies are in place to effect more complete coverage of potential loses. Additionally, owners may avoid potential liability by focusing on the practical aspects of technology deployments. For example, many Owners utilize security cameras to monitor parking pay machines. Itís likely that at many of these locations such surveillance cameras are positioned in a way that captures an image of an individualís credit card being inserted into the pay station. Itís unlikely, however, that many of the Owners of such properties have considered whether the orientation, resolution, and frame rate of a security camera, and how such security footage is stored create any sort of significant liability. In fact, itís unlikely to even cross a property owner or managerís mind, until law enforcement identifies the existence of such protected information on the Ownerís system after an attack, when significant third-party liability to the card holders has been created. From a practical perspective however, the significant expenses of this type of data loss could have been avoided by practical consideration of how and where building technology is deployed.
This Week’s Sponsor
RestorePoint, a Palo Alto Networks Platinum Partner, was part of the first wave of Traps Certified MSSP partners in North America. Traps, Palo Alto Networkís Advanced Endpoint Protection, replaces traditional antivirus with Multi-Method Prevention that pre-emptively blocks known and unknown cyber threats from compromising endpoints. To learn more, please visit us at www.restorepoint.net/traps.
Read Next
 3/27/2025
3/27/2025
The Convergence of Edge Computing, Cloud, and AI in Building Automation and Smart Buildings In the built environment, we have seen the convergence of Operational Technology (OT) and Information Technology (IT), later expanding to include Workplace Technologies (WP).
 3/27/2025
3/27/2025
DC Power: A Holistic Approach to Energy Savings in Commercial Buildings In today's energy-conscious world, businesses constantly seek ways to reduce their carbon footprint and operational costs.
 3/13/2025
3/13/2025
How to Achieve Eco-Friendly Facility Management Commercial real estate operators and facility managers are focusing on sustainable practices to minimize environmental impact, create healthier workplaces, improve productivity and lower operational costs.
 1/23/2025
1/23/2025
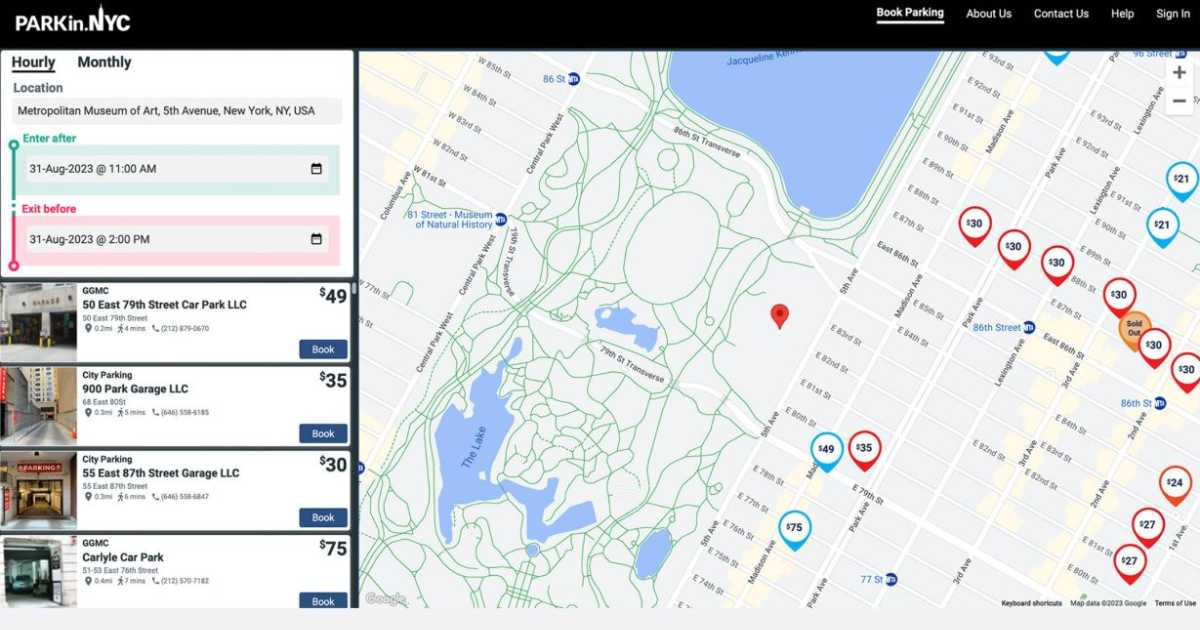
When It Comes To Managing Propertiesí Parking, Technology Is Key Itís easy for developers and real estate owners to think of parking as a necessary evil. They know they have to provide it (often, because itís mandated by code), they understand that prospective tenants and buyers expect to be provided parking, but they havenít figured out how to maximize its value.


.gif)